Advanced Apple Debugging & Reverse Engineering, Chapter 31
Por um escritor misterioso
Descrição
In this chapter, you'll use DTrace to hook objc_msgSend's entry probe and pull out the class name along with the Objective-C selector for that class. By the end of this chapter, you'll have LLDB generating a DTrace script which only generates tracing info for code implemented within the main executable that calls objc_msgSend.
Tampering and Reverse Engineering on iOS - OWASP MASTG

Advanced Apple Debugging & Reverse Engineering, Chapter 1: Getting Started

Mastering Malware Analysis

Advanced Apple Debugging & Reverse Engineering, Chapter 31: DTrace vs. objc_msgSend
Reverse Engineering Keys from Firmware. A how-to
Sony, Rootkits and Digital Rights Management Gone Too Far - Microsoft Community Hub
Advanced Apple Debugging & Reverse Engineering, Chapter 1: Getting Started
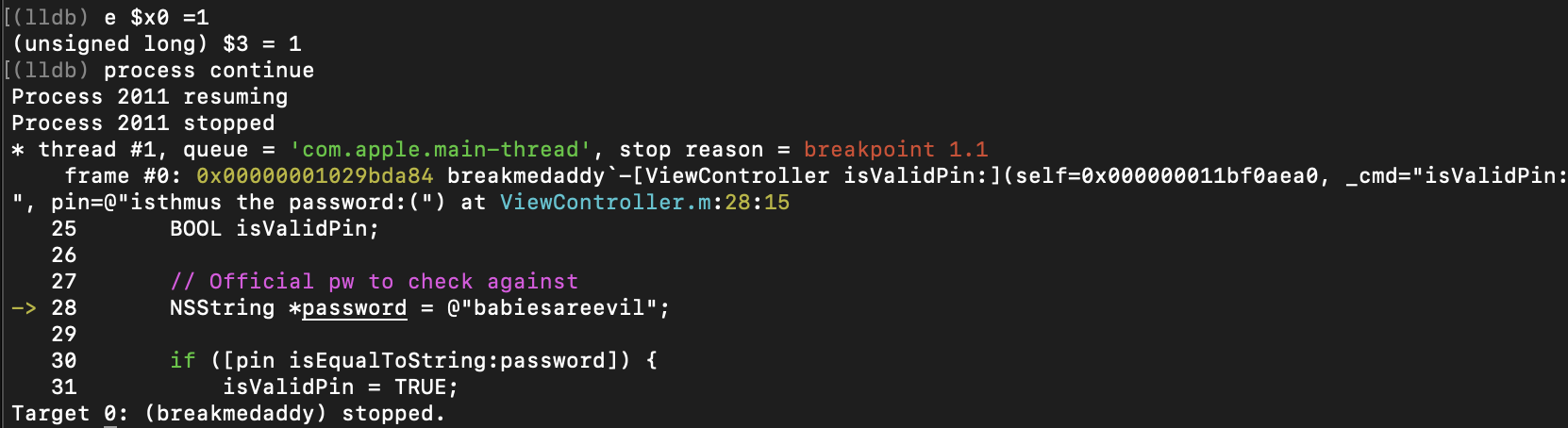
How to Reverse Engineer and Patch an iOS Application for Beginners: Part I

Blue Fox: Arm Assembly Internals and Reverse Engineering: Markstedter, Maria: 9781119745303: : Books
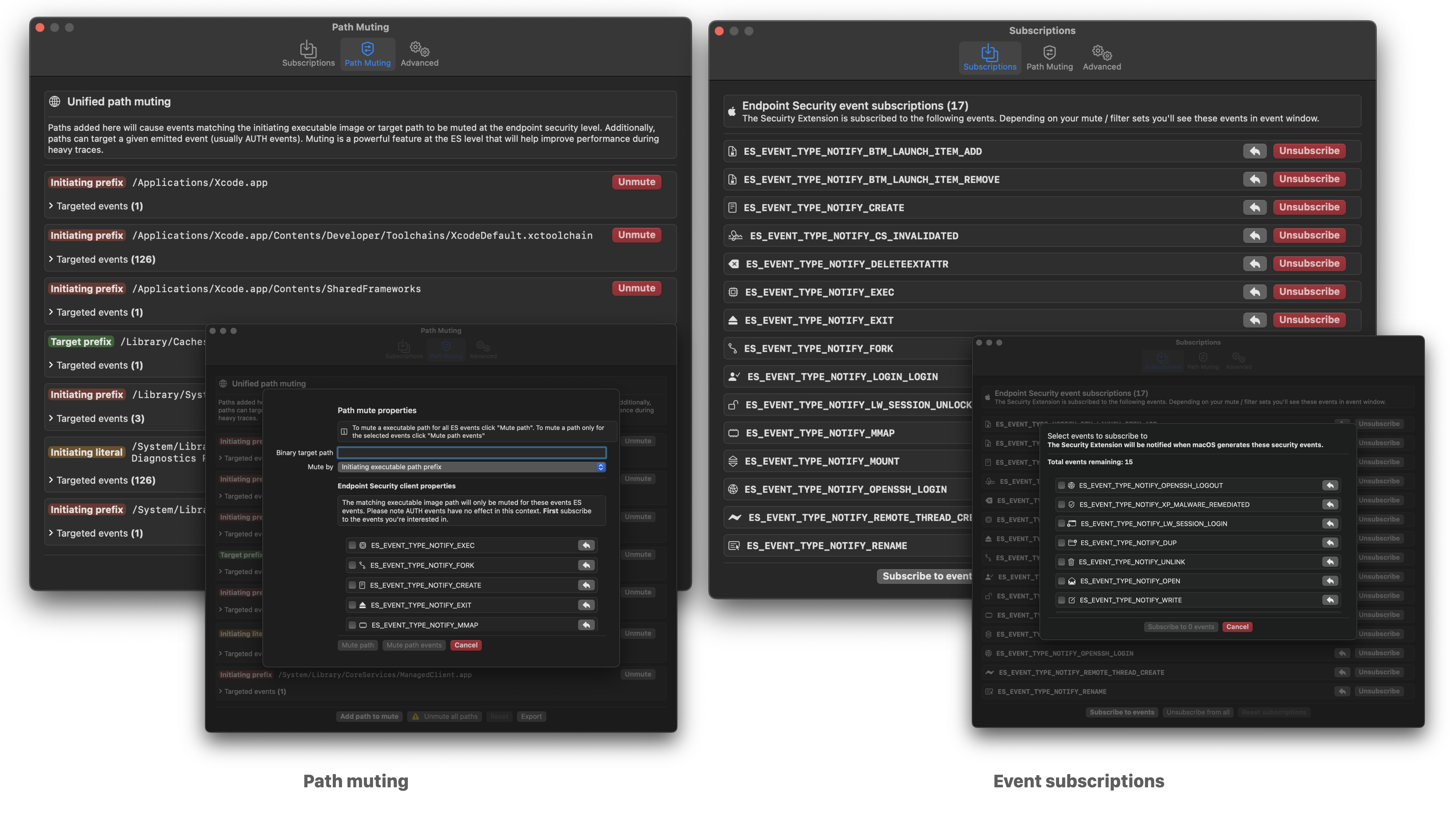
Red Canary Mac Monitor - An Advanced, Stand-Alone System Monitoring Tool Tailor-Made For macOS Security Research

Advanced Apple Debugging & Reverse Engineering, Chapter 1: Getting Started

Mastering Reverse Engineering

Reverse Engineering of a Not-so-Secure IoT Device
de
por adulto (o preço varia de acordo com o tamanho do grupo)