Conceal Threat Alert: Phishing Attack Bypasses Traditional Controls, ConcealBrowse to the Rescue
Por um escritor misterioso
Descrição
Attackers continue to innovate in their efforts to bypass traditional security controls and deliver credential theft links to unsuspecting users. In an environment rich with information about how security controls work and what entices users to click, there is a distinct need for improved protection in the browser.

The Ultimate Guide to Email Phishing - Email Uplers
What Is Email Phishing? Protect Your Enterprise

New phishing attack uses Morse code to hide malicious URLs - CCARA
Phishing - Health Information Technology

What is Trap Phishing?
Phishing Attacks - Do's and Don'ts to Protect Your Company

KOSIN Safe Sound Personal Alarm, 3 Pack 145DB

Conceal on LinkedIn: Conceal Threat Alert: Phishing Attack

Conceal on LinkedIn: Conceal Threat Alert: Phishing Attack
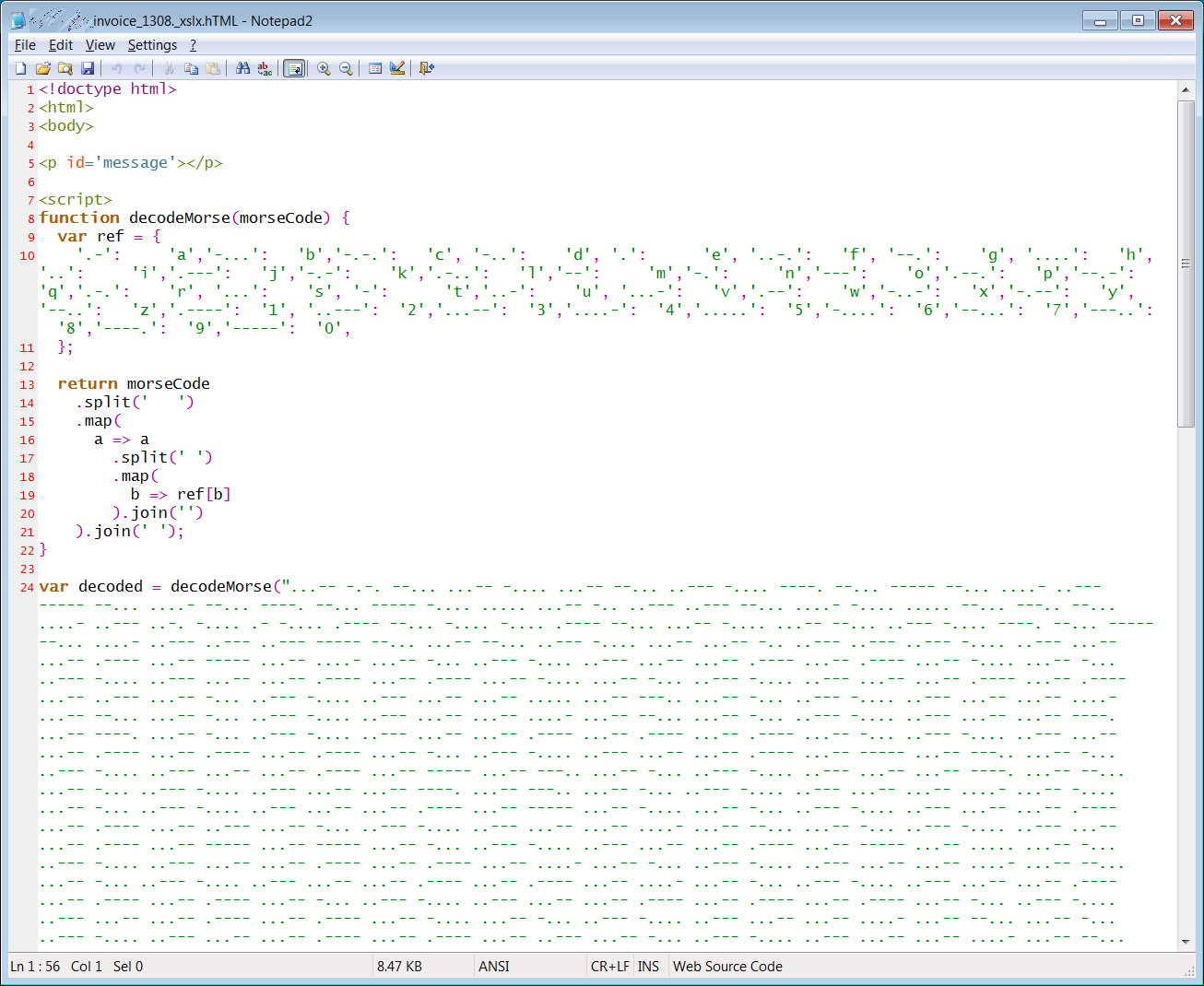
New phishing attack uses Morse code to hide malicious URLs

What is Phishing? Types of Phishing Attacks
de
por adulto (o preço varia de acordo com o tamanho do grupo)