Utilizing Morse Code to Evade Signature Based Detection Systems
Por um escritor misterioso
Descrição

PDF] Morse code based Secured Authentication System using Eye Blink through Haar Cascade and Facial Landmark Algorithm
Could WWII morse code operators detect a spy's accent on the line? - Quora

Signature-Based Morse Code Encoding for a LED-Based optical Layer 2 data communication

Plagiarism - Wikipedia

Certified Secure - Ineffective Detection Systems

Hackers are using Morse code to bypass phishing controls
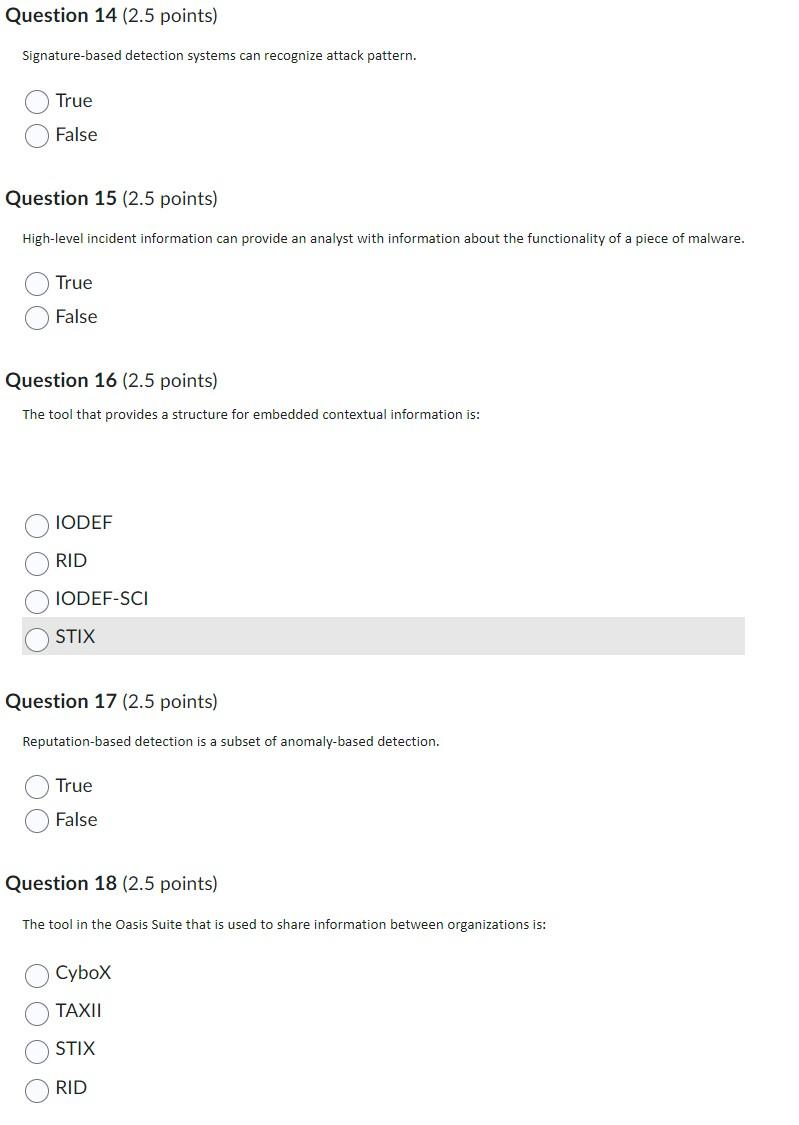
Solved Signature-based detection systems can recognize

Implementation of a Digital Signature in Backward-Compatible QR Codes Using Subcell Division and Double Encoding

New phishing attack uses Morse code to hide malicious URLs - CCARA

Hackers Bypass Firewalls Restrictions Using CloudFlare Tunnels
Conception of recoding the international Morse code for information
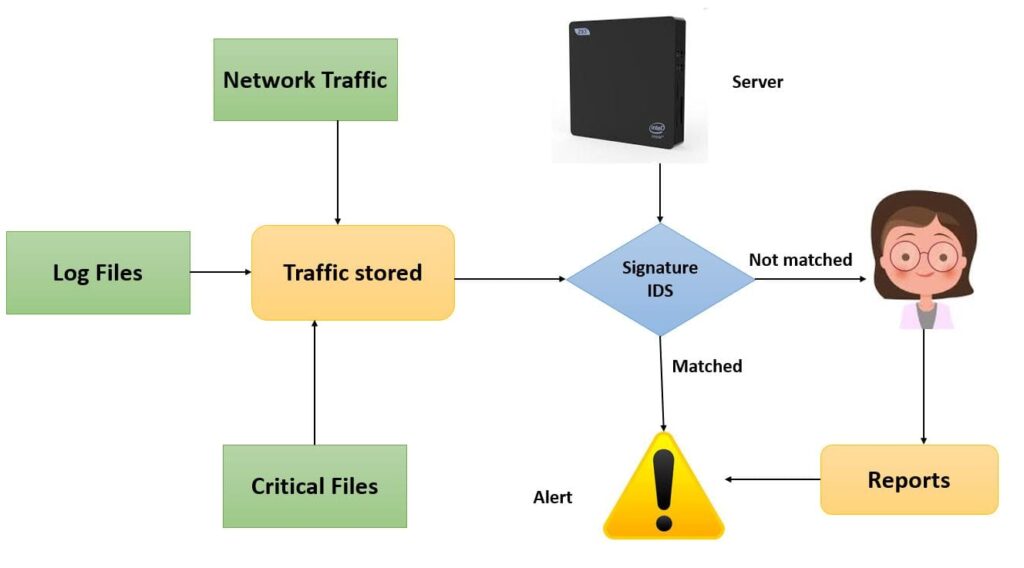
What is Intrusion Detection System [IDS]? - UseMyNotes

Volume 2-issue-6-2037-2039
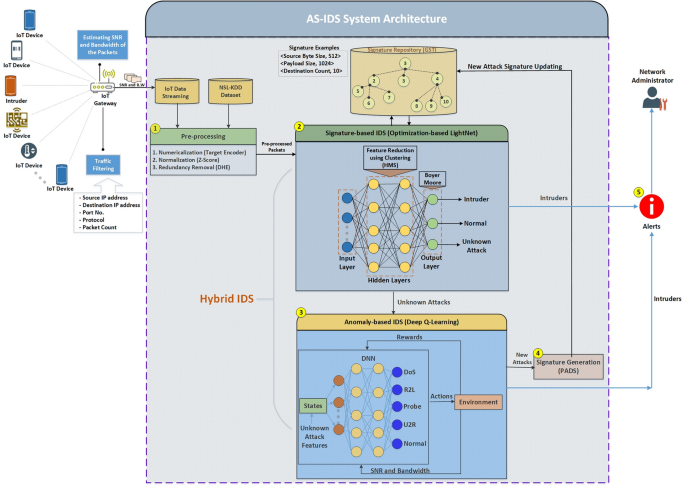
AS-IDS: Anomaly and Signature Based IDS for the Internet of Things

The Art & Science of Threat Hunting - A Guide to Preventing Cyber Attacks
de
por adulto (o preço varia de acordo com o tamanho do grupo)